
Developing a strong defense-in-depth OT cybersecurity can be challenging and complex, but it doesn’t have to be. In this engaging eBook see how to advance your OT cybersecurity maturity with real-world examples of deployments that work.
Join Itay Glick, VP of Product, and János Rotzik, Product Marketing Manager at OPSWAT, as they show you how OPSWAT MetaDefender Email Security takes your email security posture to the max with its advanced capabilities, protecting you from zero-day exploits and sophisticated email-borne threats.
Takeaways will include:
- Cyber-attack challenges:
Learn about the difficulties posed by sophisticated cyber-attacks. - Advanced capabilities:
Discover OPSWAT's key technologies to maximize your protection against these challenges. - How to enhance Microsoft 365 Exchange Online Protection:
Understand why OPSWAT is the ideal solution to provide robust email protection.
Register now and take the first step to move your email security posture to the max!
Start Learning from Successful Deployments
Here’s what you’ll learn in this eBook:

The Cybersecurity Maturity Curve
See what it takes to advance your own OT cybersecurity and learn how to get started.
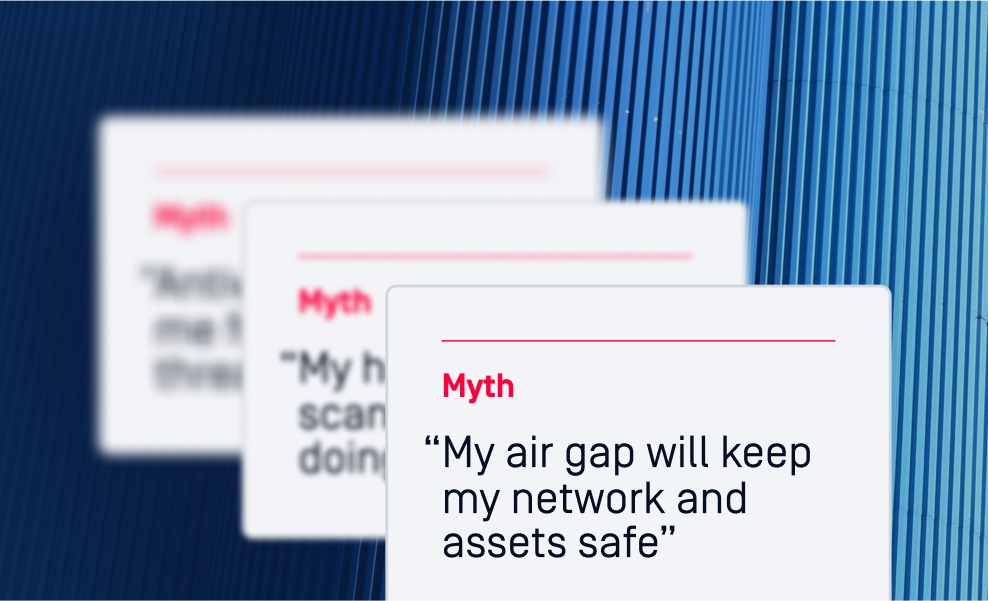
The Myths of OT Cybersecurity
We break down some common OT cybersecurity myths to make sure you’re making decisions based on fact.
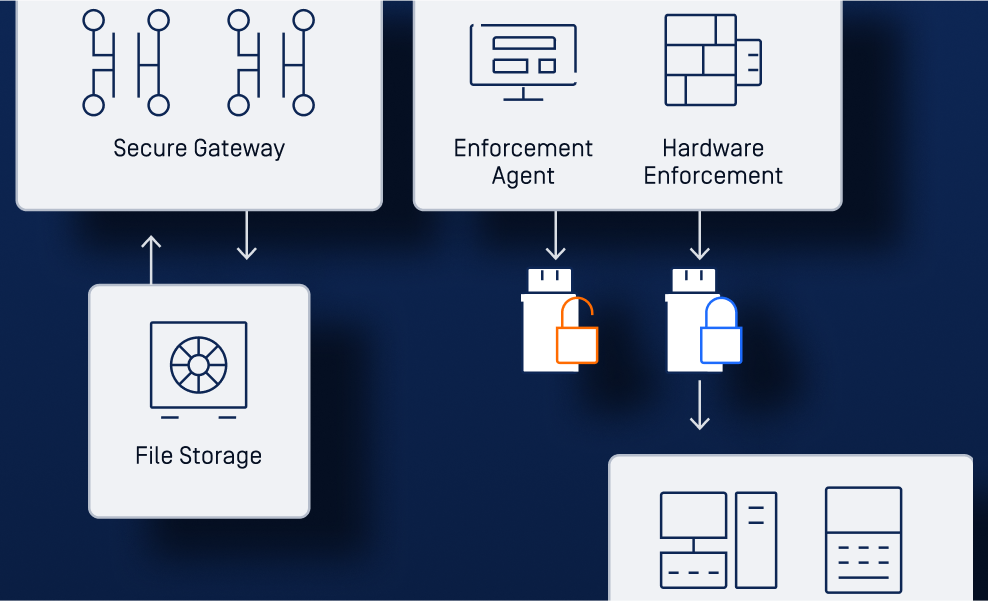
Real World Deployments
Explore detailed examples of how industries around the world are using OPSWAT solutions to protect their OT environments.
