Comprehensive - Gain full control over a host of functions including the state of security applications and their vulnerabilities
Effective - Access agile and granular policy control tools that empower implementation within your organization
Proven - Leverage the technology that has been trusted on over 100 million enterprise endpoints
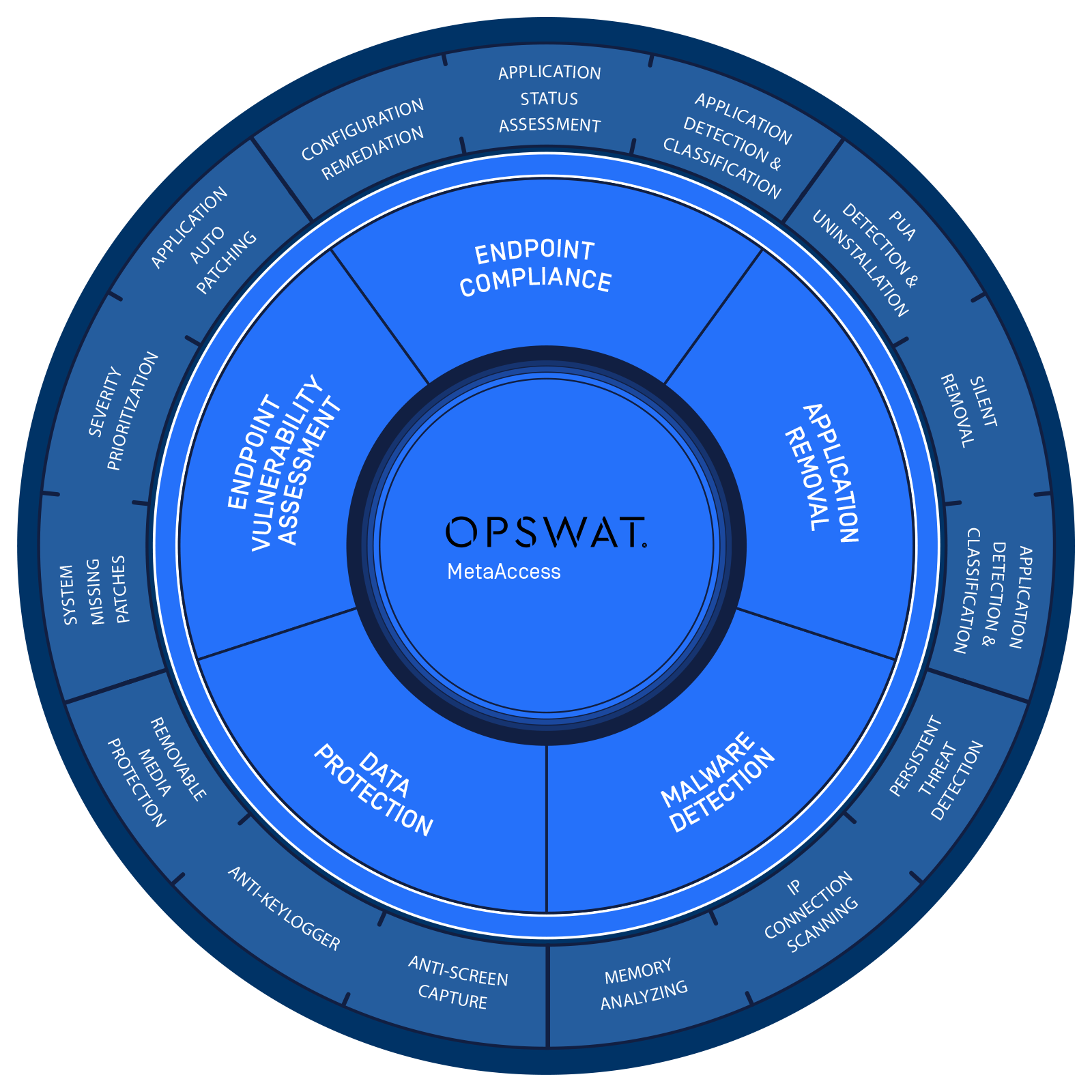
Detect, classify, and manage 5,000+ security applications
Silently remove thousands of applications including toolbars and public sharing software
Detect vulnerabilities in over 20,000 applications and block devices if critical
Inspect endpoints with a quick memory scan or full file system scan; discover persistent threats with local antimalware log analysis
Protect removable media usage; block keystroke and screen logging
"MetaAccess enables us to provide our many users with increased usability and secure network and resources access, while maintaining a high level of security for the bank's network."
Large Global Bank

MetaAccess is an endpoint compliance and security platform that prevents risky devices from accessing local networks and cloud applications such as Office 365, Salesforce and Dropbox.
Comprehensive - Gain full control over a host of functions including the state of security applications and their vulnerabilities
Effective - Access agile and granular policy control tools that empower implementation within your organization
Proven - Leverage the technology that has been trusted on over 100 million enterprise endpoints

Detect, classify, and manage 5,000+ security applications
Silently remove thousands of applications including toolbars and public sharing software
Detect vulnerabilities in over 20,000 applications and block devices if critical
Inspect endpoints with a quick memory scan or full file system scan; discover persistent threats with local antimalware log analysis
Protect removable media usage; block keystroke and screen logging
"MetaAccess enables us to provide our many users with increased usability and secure network and resources access, while maintaining a high level of security for the bank's network."
Large Global Bank

MetaAccess delivers visibility, control, and compliance for every device before they access your applications
Visibility - Gain full visibility of endpoints including the state of security applications and their vulnerabilities
Control - Automatically check the widest set of access control policy options and checks in the industry
Compliance - Based upon customized policies, block non-compliant devices from accessing until the user of the device has self-remediated

Detect, classify, and manage 5,000+ security applications
Silently remove thousands of applications including toolbars and public sharing software
Detect vulnerabilities in over 20,000 applications and block devices if critical
Inspect endpoints with a quick memory scan or full file system scan; discover persistent threats with local antimalware log analysis
Protect removable media usage; block keystroke and screen logging
"MetaAccess enables us to provide our many users with increased usability and secure network and resources access, while maintaining a high level of security for the bank's network."
Large Global Bank
